Dell Wyse Windows 10 LTSC automatic update script
Keeping Windows up to date on the latest security patches is a big part of maintaining a secure network. Dell Wyse thin clients are normally maintained by a Wyse Management Suite, but WMS was found to not have a reasonable solution for installing Windows updates on a schedule that would work for all of their thin client models running Windows 10 LTSC. This can be troublesome for those that need to maintain these units to ensure that they're both secure and stable.
As anyone who's administered these units should know, Dell Wyse thin clients running Windows LTSC come with a Unified Write Filter, or UWF, that's enabled by default. This application reverts any changes that were made during a user's session once the thin client has been rebooted. A useful tool to prevent users from making any changes or saving files to the thin client itself. Unfortunately this also prevents system applications, such as Windows Update, from making changes as well. To make matters worse, Windows will still attempt to install these updates and if it falls too far behind, this tends to trigger an error with the Unified Write Filter that's shown below.
The system is running out of available memory. Once the Critical threshold is crossed, the system will reboot immediately. Please save your work.
When the above error occurs, the thin client will undergo a spontaneous reboot shortly after. This then repeats itself frequently. As the Windows Update application attempts to install patches to the thin client repeatedly. Quickly becoming a troublesome experience for the user.
An update to WMS was later released to introduce a UWF Servicing mode that could be used to trigger updates to install on the Windows 10 LTSC thin clients. However, this solution came with a number of stipulations. One being that it's a pro feature within WMS that requires a paid license. The other issue was that it's not compatible with older Wyse thin client models. Such as the Wyse 5070 that couldn't be updated to the required June 2022 release of Windows 10 LTSC. Dell Support unfortunately offered no alternative solution to installing Windows updates that would be compatible for all Wyse thin client models.
With these road blocks in place, a third party solution needed to be created that could accomplish the task of maintaining Windows updates on the Windows LTSC thin clients. This article will outline the PowerShell script that was designed to accomplish this task by creating three batch files that'll temporarily disable the UWF on the thin client, install the Windows updates that are pending via the use of PowerShell commands, and then re-enable the UWF again after allowing a sufficient amount of time for this process to complete. All of these will be set to run as scheduled tasks within Windows on the thin client itself. Updates that were successful and unsuccessful will also be logged within text files and preserved for a number of days. This solution was tested and confirmed as working on Dell Wyse 5070 and 3000 series thin clients running Windows 10 LTSC.
Download the PowerShell script and customize settings
The PowerShell script to install the batch files and scheduled tasks associated with updating Windows automatically on the Wyse thin clients can be downloaded below. Extract the ZIP file after downloading and run the file titled wyse-update.ps1 as Administrator and with the UWF disabled on each thin client that would need this solution applied. This task will only need to be completed on each thin client once to set it up for installing Windows updates automatically.
The PowerShell script is designed to setup tasks that'll install Windows updates on a weekly schedule. This may require adjustments based on needs and business hours. You'll want to select a date and time when the thin clients are online, but also during a time when the thin clients are not being utilized by any users. The process does require reboots that'll occur without warning. The PowerShell script is also configured to create and preserve logs for the Windows updates that were successful or unsuccessful during each time the scheduled task is ran. The script contains a variable that can be adjusted to set how many days worth of logs you'd like to preserve before they're purged from the system. The PowerShell script has a series of defaults already in place that are explained below.
- The Unified Write Filter is disabled and the system is rebooted on Sunday at 1:00 AM.
- Windows will then install updates on Sunday at 1:30 AM. Allowing 30 minutes for the thin client to return to an online state. A reboot is also scheduled to occur in 30 minutes after this command completes. Any logs older than 180 days are also deleted at this time.
- The Unified Write Filter is enabled on Sunday at 5:00 AM. Allowing enough time for the update procedures to complete.
It's worth noting the significant amount of time between installing Windows updates (1:30am) and re-enabling the unified write filter (5:00am.) This is to allow enough time for Windows Update to install the patches without being interrupted by the enabling of UWF. This will need to be considered if any adjustments to the date and time defaults are necessary. It may also be beneficial to run Windows Update manually prior to installing this script. So that there's less likely an occurrence of the script installing a large group of patches during its initial run.
DownloadAfter downloading and extracting the ZIP file, the above defaults can be changed by editing the variables located in the wyse-update.ps1 file. You may open this file in a text editor of your choice or by right clicking the file in Windows to select the Edit option from the context menu. This will open the file for editing using the Windows PowerShell ISE application. Locate the seven variables on lines 16 through 25 that'll need adjustment. A description of each of these variables is located below. Along with being detailed within the file itself.
- $keep_days
- This is the number of days each text file log will be preserved for before being purged from the system.
- $uwf_off_date
- This is the day of the week that UWF will be turned off to prepare for the installation of Windows updates.
- $uwf_off_time
- This is the time of the day that UWF will be turned off. Specified in a 24 hour format.
- $update_date
- This is the day of the week when Windows updates will be installed.
- $update_time
- This is the time of the day that Windows updates will be installed. Specified in a 24 hour format.
- $uwf_on_date
- This is the day of the week when UWF will be turned on after the Windows updates have completed.
- $uwf_on_time
- This is the time of the day when UWF will be turned back on. Specified in a 24 hour format.
In the event that the solution needs to be reverted on the thin client, the batch files and scheduled tasks that were installed can be removed by running the other PowerShell script titled wyse-update-uninstall.ps1 with the unified write filter disabled on each Wyse thin client. Please note that the uninstall script will also remove the LOGS directory as well. You may wish to copy these logs to a new location prior to proceeding with the removal if you'd like to preserve this information.
Deploying the solution to the Wyse thin clients
As stated in the first section of this article, the PowerShell script will need to be run on all applicable Wyse thin clients that'll need to install Windows updates automatically. This can be a tedious task to accomplish manually depending on the total number of thin clients that are on the network running Windows LTSC. The Wyse Management Suite has the ability to upload and run PS1 files via App Policies. This feature can be used to deploy this solution to the thin clients by following the steps below.
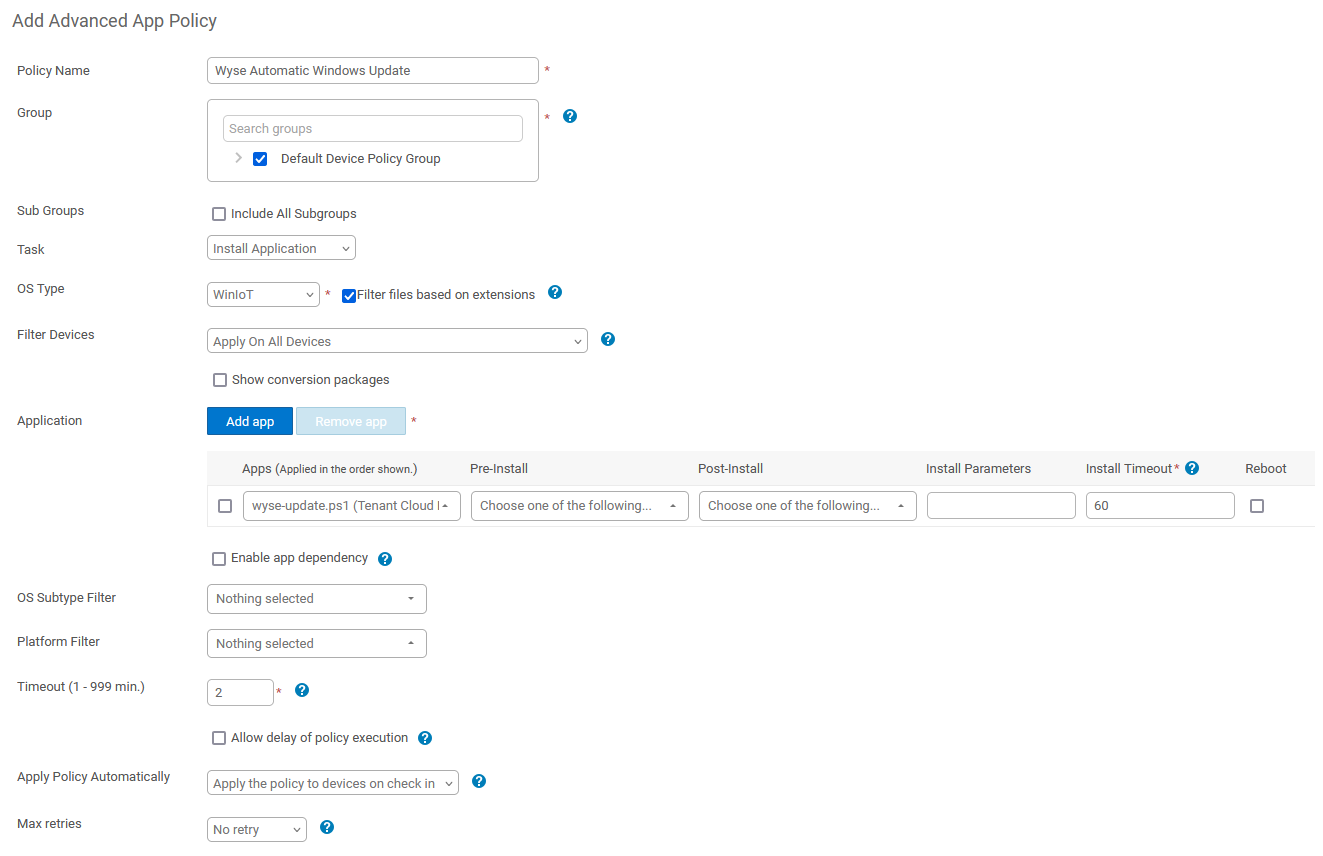
- Log into WMS and click on the Apps & Data tab.
- Click Thin Client under App Inventory and select Add WinIoT Package File.
- Browse to and upload the wyse-update.ps1 file to the repository.
- Click Thin Client under App Policy and select Add Advanced Policy.
- Select the Group from the list containing the Wyse thin clients you'd like to roll this solution out to and match the rest of the settings shown in figure 1 below.
- Click Yes on the prompt alerting you that the policy will not be editable.
- Select the Jobs tab at the top and click the button that says Schedule App Policy.
- Select the newly created policy from the drop down menu and set it to run immediately or at a desired time.
It was found that WMS can be unreliable at times completing installations via the App Policies. If you're noticing that some thin clients are not proceeding with the installation, you may want to pursue a different option than the above steps. Dell support unfortunately didn't provide any insight on why some thin client would not run the App Policy they were configured for. The best option would be to use an RMM solution that's capable of running agent procedures. Such as Kaseya VSA. Your RMM solution would already have to be installed on the thin clients in order for this option to be available to you. Otherwise manual deployment would be your only option. This involves logging into each thin client, disabling UWF, running the PowerShell script as administrator, and re-enabling UWF once this has been completed.
Analyzing logs generated by Windows update procedures
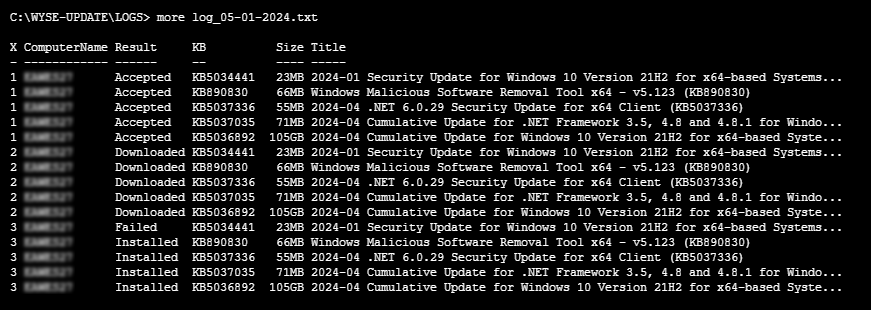
A text file log is created each time a thin client installs Windows updates via use of this script. These logs are located in the directory C:\WYSE-UPDATE\LOGS and are preserved for a total of 180 days by default. See notes above in section one for details on how to change this default setting.
Log files are named with the date that corresponds with each day that Windows updates were installed. This will allow one to determine which updates were installed on any given day or to keep track of an update that has been consistently failing. Figure 2 below shows an example log from May 1st, 2024 outputted using the More command. This is a useful method to check logs if you have Telnet or SSH access to the thin client. These logs can also be opened for viewing in any text editor. Such as Notepad. Below you'll see the KB numbers of each Windows Update that was accepted and downloaded. Along with the final result being either failed or installed.